Attached files
| file | filename |
|---|---|
| 8-K - BlackRidge Technology International, Inc. | blackridge.htm |
Exhibit 99.1

BLACKRIDGE TECHNOLOGY NEXT GENERATION CYBER DEFENSESEPTEMBER 2017 INVESTOR PRESENTATION

SAFE HARBOR THIS DOCUMENT WAS PREPARED BY BLACKRIDGE TECHNOLOGY, AND MAY CONTAIN FORWARD-LOOKING STATEMENTS, WHICH INVOLVE KNOWN AND UNKNOWN RISKS, UNCERTAINTIES, AND OTHER FACTORS, WHICH MAY CAUSE BLACKRIDGE’S ACTUAL RESULTS, PERFORMANCE, OR ACHIEVEMENTS TO BE MATERIALLY DIFFERENT FROM FUTURE RESULTS EXPRESSED OR IMPLIED BY THE FORWARD LOOKING STATEMENTS CONTAINED HEREIN. SOME OF THE RISKS WHICH MAY CAUSE BLACKRIDGE’S PERFORMANCE TO DIFFER FROM THE FORECASTED RESULTS INCLUDE, BUT ARE NOT LIMITED TO, DELAYS IN TECHNOLOGY DEVELOPMENT, DELAYS OR CANCELLATIONS OF PENDING PURCHASE ORDERS OR OTHER REVENUE, HIGHER THAN EXPECTED COSTS, ACTIONS TAKEN BY CREDITORS OR VENDORS OF THE COMPANY [INCLUDING LITIGATION] WHICH ARE NOT EXPECTED AND CHANGES IN THE OVERALL MARKET FOR CYBERSECURITY SOFTWARE PRODUCTS. THE COMPANY MAY FACE ADDITIONAL RISKS THAT WE HAVE NOT LISTED. WE UNDERTAKE NO OBLIGATION TOUPDATE ANY FORWARD-LOOKING STATEMENTS AFTER THE DATE OF SUCH STATEMENTS.

[NET MARGINS]: ~65-70% 3 SYMBOL PRICE MARKETCAP Gross Margins CASHBURN C&CE BRTI $1.45 ~90-92% $46MM $0.4MM $2.5MM BLACKRIDGE AT A GLANCE BlackRidge authenticates identity and enforces security policy on the first packet, before a network session is establishedBlackRidge First Packet Authentication™ stops attacks at the earliest possible timeCURRENT SECURITY PRODUCTSSTART AFTER NETWORK SESSIONS ARE ESTABLISHED MONETIZING A DESIGN FLAW IN NETWORK SECURITY [COGS]: ~7-10% FINANCIAL SNAPSHOT: DENOTES BLACKRIDGE PRESENCE *PRICE/MARKET CAP AS OF 9/7/17

BLACKRIDGE CORPORATE DEVELOPMENT 4 DEVELOPMENT IN MOTION BLACKRIDGE COMPLETES REVERSE MERGER INTO GROTE MOLEN, [OTC:GROT], A FULLY REPORTING, 9 YEAR OLD OPERATING PUBLIC COMPANY WITH IP ASSETS, REVENUES AND EBITDA FINRA APPROVES CHANGE OF NAME FROM GROTE TO BLACKRIDGE TECHNOLOGY INTERNATIONAL, INC. “BRTI” STARTS TRADING OTC UNDER BRTI AND MARKET MAKERS START QUOTING MARCH THROUGH MAY 2017 FILINGS: SUPER 8K, 10K, Q1 2107 10Q, PROXY, S-8; COMPLETE APA TO SELL GROTE ASSETS TO GROTE FOUNDERS AND TAKE CONTROL OF GROTE MANAGEMENT AND MERGE CAP TABLES DTC ELIGIBLE, FINRA ISSUES NEW TICKER MARCH 2017 JUNE 2017 JULY 2017 MARCH-MAY 2017 JUNE 2017 BLACKRIDGE FORMS BLACKRIDGE BLOCKCHAIN CORP., EXPECTED COMPLETION SEPTEMBER 2017 SEPTEMBER 2017 EXPECTED COMPLETION OF BALANCE SHEET RESTRUCTURING INITIATIVES NOVEMBER 2017 EXPECTED NASDAQ UPLISTING Q1 2018

MONETIZING A DESIGN FLAW IN NETWORK SECURITY DIFFERENTIATION DRIVEN VALUE-ADD

FIRST PACKET AUTHENTICATION™ EVOLVING CYBER SECURITY
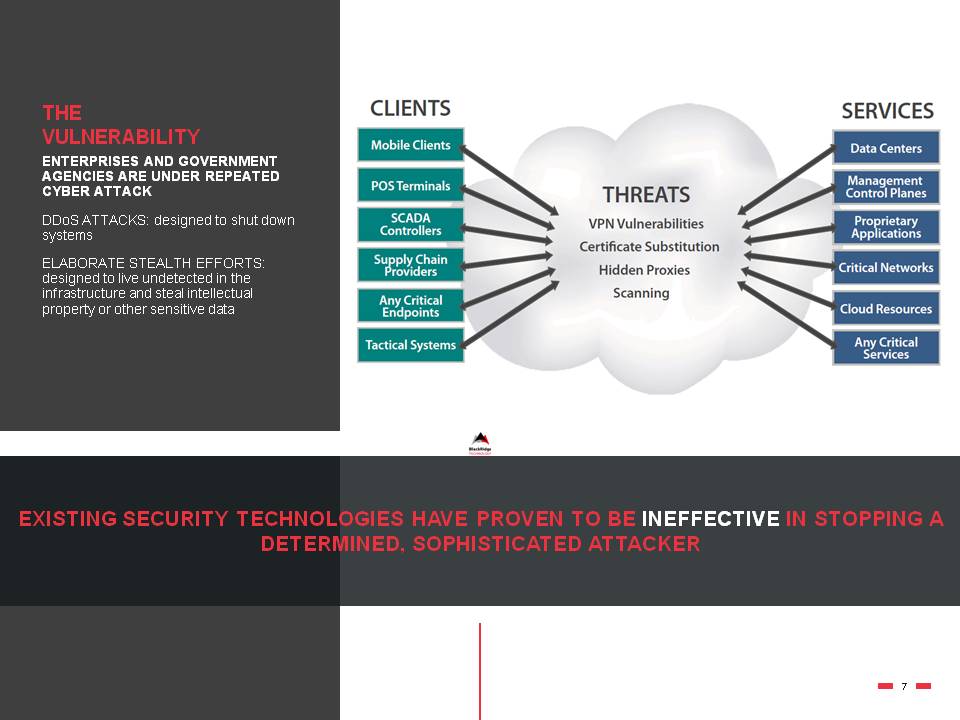
THE VULNERABILITY ENTERPRISES AND GOVERNMENT AGENCIES ARE UNDER REPEATED CYBER ATTACK DDoS ATTACKS: designed to shut down systemsELABORATE STEALTH EFFORTS: designed to live undetected in the infrastructure and steal intellectual property or other sensitive data EXISTING SECURITY TECHNOLOGIES HAVE PROVEN TO BE INEFFECTIVE IN STOPPING A DETERMINED, SOPHISTICATED ATTACKER 7

TECHNOLOGY DEVELOPMENT NETWORK RECON USES VULNERABILITY SCANNERS TO PROBE NETWORKS AND THE DEVICES ATTACHED TO THEMInformation is being leaked, even in the presence of firewalls includes the existence and identity of servers and network applications. VULNERABILITY/PORT SCANNERS ATTEMPT TO ESTABLISH TCP/IP CONNECTIONS TO VARIOUS NETWORK PORTS NETWORK-ATTACHED DEVICES REVEAL INFORMATION ABOUT THEIR CHARACTERISTICS SIMPLY BY RESPONDING TO THESE TCP/IP CONNECTION REQUESTS THIS INFORMATION IS EXPOSED BECAUSE EACH NETWORK-CONNECTED DEVICE MUST ESTABLISH A TCP/IP CONNECTION BEFORE PERFORMING ANY CLIENT AUTHENTICATION. 8

BLACKRIDGE PRODUCT AND PARTNER DEVELOPMENT 9 DEVELOPMENT IN MOTION DEVELOPMENT ACCELERATION PROGRAM, ARMY DOD $5M FUNDINGCORE PRODUCT DEVELOPMENTIP AND PATENT DEVELOPMENTTECHNOLOGY DEMONSTRATION PROGRAM, OSD ENTERPRISE PRODUCT DEVELOPMENTMARKET TESTS, 100G DEMONETWORK OVERLAY SOLUTION100G TAC GATEWAY DEMOS TO ARMY PEO-EIS 2011-2012 2010-2012 2013-2014 DISA UC-APL APPROVALDISA AND ARMY CONTACTS 2016-2017 INTERNATIONAL EXPANSIONSALES & MARKETING BUILDOUTSOFTWARE ENDPOINT PRODUCTSBLOCKCHAIN, IIOT, AND PUBLIC CLOUDS SUPPORT 2017-2018 CLOUD AND ENTERPRISE PRODUCT ENHANCEMENTS IBM Z SYSTEMS PARTNERSHIPCIENA, REDHAT, SPLUNK, AND MARIST PARTNERSHIPS 2015-2016

IT IS THIS DESIGN FLAW OF TCP/IP THAT ENABLES SCANNING TOOLS TO IDENTIFY WHAT NETWORK APPLICATIONS ARE PRESENT AND TO DEVELOP THE “WEAPONIZATION” AND ATTACK THE SYSTEMS
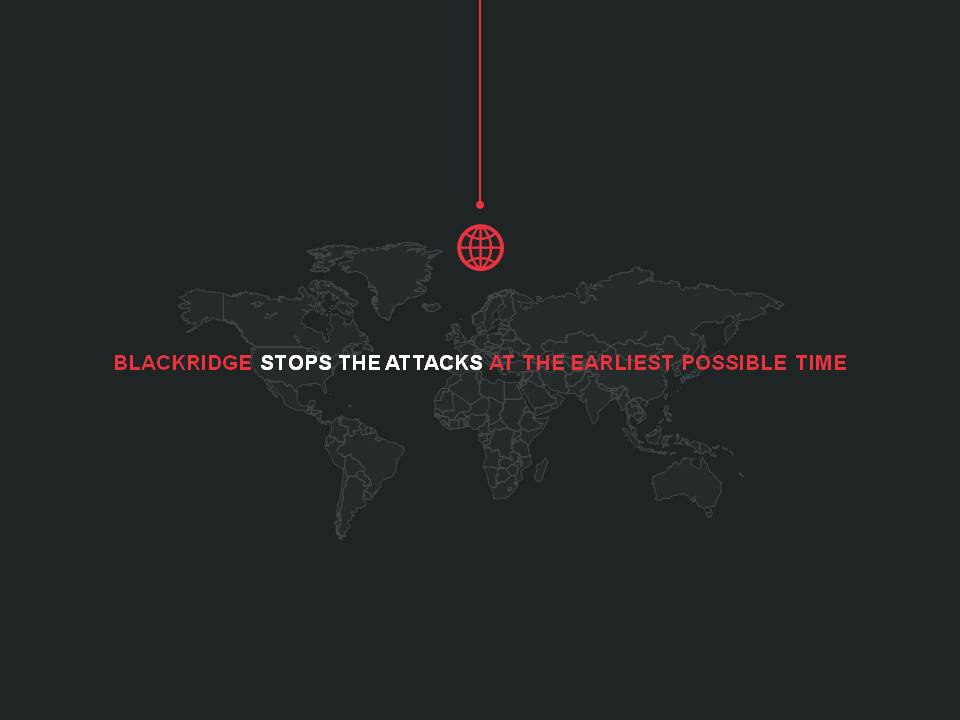
BLACKRIDGE STOPS THE ATTACKS AT THE EARLIEST POSSIBLE TIME

TRANSPORT ACCESS CONTROL CALLER-ID FOR THE INTERNET

AUTHENTICATE & ENFORCE BLACKRIDGE AUTHENTICATES IDENTITY AND ENFORCES SECURITY POLICY ON THE FIRST PACKET, BEFORE A NETWORK SESSION IS ESTABLISHEDStops port scans and network attacks Provides ROI and reduces riskAddresses network segmentation for compliance BLACKRIDGE ISOLATES AND PROTECTS SERVERS AND APPLICATIONS TCP/IP BLACKRIDGE FIRST PACKET AUTHENTICATION™ STOPS ATTACKS AT THE EARLIEST POSSIBLE TIMECURRENT SECURITY PRODUCTSSTART AFTER NETWORK SESSIONS ARE ESTABLISHED TIME Packet Flows SESSIONSETUP DATATRANSFER PORT SCANS AND ATTACKS OCCUR DURING TCP/IP SESSION SETUP 13

BLACKRIDGE:STRONG VALUE-PROP REDUCED SYSTEM COSTREDUCED NETWORK TRAFFIC LOADREDUCED COMPLIANCE COST REDUCED SYSTEM COST:REDUCES EQUIPMENT ACQUISITION COSTSREDUCES UNAUTHENTICATED TRAFFIC REDUCED NETWORK TRAFFIC LOAD:REMOVE 99.999% OF UNAUTHENTICATED TCP/IP TRAFFICREMOVE UP TO 70% OF ALL SESSIONS BEING PROCESSED BY A FIREWALL REDUCED COMPLIANCE:IMPROVED COMPLIANCEALL REQUESTS LOGGEDREGULATORY COMPLIANCE/AUDIT COMPLIANCE 14

BLACKRIDGE ADDRESSES THE TCP/IP NETWORK VULNERABILITY THAT IS EXPLOITED IN 100% OF CYBER ATTACKS
BLACKRIDGE GO TO MARKET STRATEGY ROADMAP AND DEVELOPMENT PLAN

COMMERCIAL ENTRY AND GOVERNMENT EXPANSION 17 OUR PROCESS DoD and IBM provides market credibility and initial paths to market LEVERAGE DOD AS INNOVATOR AND IBM AS EARLY ADOPTER STRONG ROADMAP AND DEVELOPMENT TEAM IN PLACE DOD/ARMY CYBER PROGRAMS RESTARTED IN 2016 Sell direct and with partners to government and enterprises First International Reseller agreement with Crimson Logic in Singapore to cover Southeast Asia and Middle East Cloud service provider and Blockchain partnerships in progress for 2H2017 offerings Channel strategy in development by ex-CISCO/VMware head of channels First DoD new projects budget passed in five years DISA in 2nd phase of testing for DoD Approved Product List Government key advisors and channel partners such as Arrow IMMIX in place First $1M order in Q3 to protect Army network in Korea - $20M total opportunity Major new releases in 2016 and 2017Roadmap and positioning reviewed by Gartner and other industry analystsAdditional patents to be filed
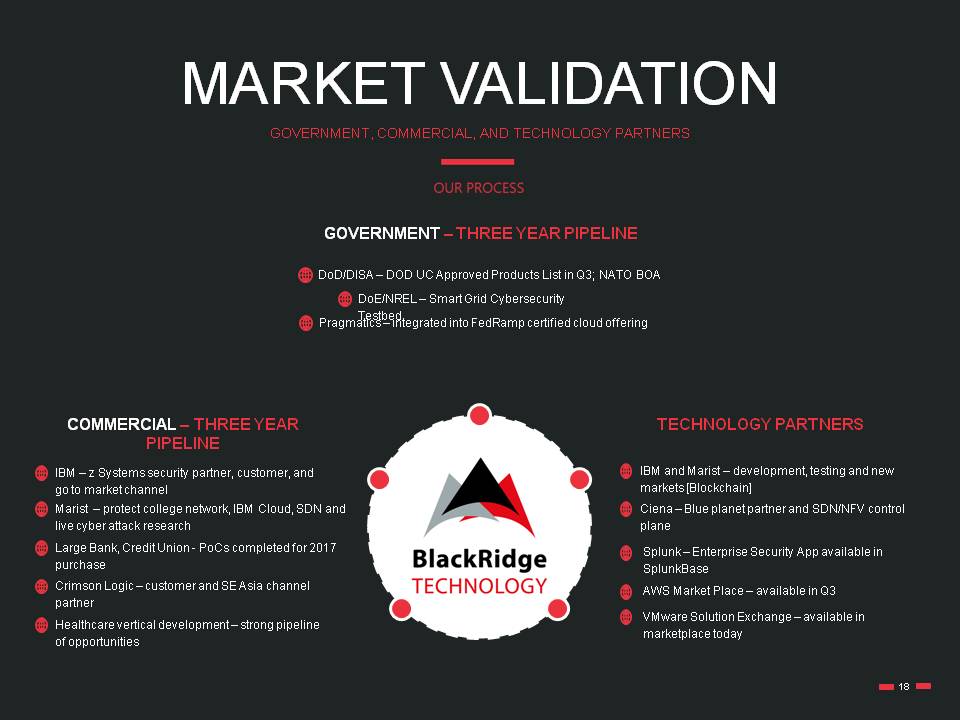
MARKET VALIDATION GOVERNMENT, COMMERCIAL, AND TECHNOLOGY PARTNERS DoD/DISA – DOD UC Approved Products List in Q3; NATO BOA GOVERNMENT – THREE YEAR PIPELINE TECHNOLOGY PARTNERS COMMERCIAL – THREE YEAR PIPELINE DoE/NREL – Smart Grid Cybersecurity Testbed Pragmatics – integrated into FedRamp certified cloud offering IBM – z Systems security partner, customer, and go to market channel Marist – protect college network, IBM Cloud, SDN and live cyber attack research Large Bank, Credit Union - PoCs completed for 2017 purchase Crimson Logic – customer and SE Asia channel partner IBM and Marist – development, testing and new markets [Blockchain] Healthcare vertical development – strong pipeline of opportunities Ciena – Blue planet partner and SDN/NFV control plane Splunk – Enterprise Security App available in SplunkBase AWS Market Place – available in Q3 VMware Solution Exchange – available in marketplace today 18

UNLIKE MANY CYBER SECURITY STARTUPS, BLACKRIDGE HAS FOCUSED ON MONETIZING EACH ENGAGEMENT; WHILE SECURING LONG-TERM, RECURRING REVENUE

20 $93B2018 WORLDWIDE SPENDINGThe latest forecast from Gartner, Inc. predicts worldwide information security spending will grow ~7% to reach $86B in 2017 and will climb to $93B in 20181 $1T5Y CUME SPENDING 2017-2021Global cybersecurity spending is predicted to exceed $1T cumulatively over the next five years, from 2017 to 20212 $6TANNUAL CYBER CRIME LOSS The world will suffer $6T in annual cyber crime damages by 2021; up from $3T in 20152 Dollars invested in these companies in Q2’17 were the highest of any quarter over the time period tracked. Clocking in at $1.6B, Q2’17 is the fifth quarter in which funding to private cybersecurity companies crossed the $1B mark.4 QUARTERLY FINANCING TRENDS 100+ On a quarterly basis, deals to cybersecurity startups nearly tied the record last quarter, with 145 disclosed equity funding rounds in Q2’17. Deals have exceeded 100+ each quarter since Q4’1534 TAMMARKET INVESTMENT 1 Gartner, Inc.2 Cybersecurity Ventures3 EX. Q4/20164 CB Insights5 Through 6/30/2017; NOT annualized 3 3 DISCLOSED FUNDING IN MILLIONS 5

PATENT PORTFOLIO CREATING DEFENSIBLE LEADERSHIP AND MARKET SHARE

IP STRATEGY DISRUPTIVE, PATENT PROTECTED TECHNOLOGY *See appendix for patent details 22
BLACKRIDGE HAS FOCUSED ON DEVELOPING ITS INTELLECTUAL PROPERTY PORTFOLIO SINCE INCEPTION, KNOWING THAT ITS VALUE WOULD BE DERIVED PRIMARILY FROM CREATING DEFENSIBLE LEADERSHIP

FIRST TO MARKET WITH A NEW APPROACH TO CYBER DEFENSE INVESTMENT SUMMARY STRONG INTELLECTUAL PROPERTY PORTFOLIO; 3-5 YEAR LEAD ON COMPETITION STRONG PRODUCT DEVELOPMENT PIPELINE: 2018: RELEASE OF BLOCKCHAIN PRODUCT INNOVATOR IN CYBER DEFENSE SOLUTIONS 2016: INITIAL COMMERICAL PRODUCT RELEASE 2H 2017 V4.1 PRODUCT RELEASE PROVEN MANAGEMENT TEAM DOD APPROVAL – GOLD STANDARD 24
Chris Tyson – MZ Group North America chris.tyson@mzgroup.us 949-491-8235 Please contact us with any questions or for more information CONTACT DISRUPTIVE, PATENT PROTECTED TECHNOLOGY

APPENDIX

MEET OUR TEAM 27 BLACKRIDGE MANAGEMENT CEO or Senior Executive at DEC, Adaptec, Sun Bob Graham Co-Founder Alteon WebSystems. Inventor of TAC, 8 patents John Hayes Public Company experience, Lehman brothers. SEC John Bluher CIO Xsigo, CIO/SVP Micromuse, IDS/IDMS security startups Bruce Fingles CEO/Founder CTO/Founder CFO SVP - Operations
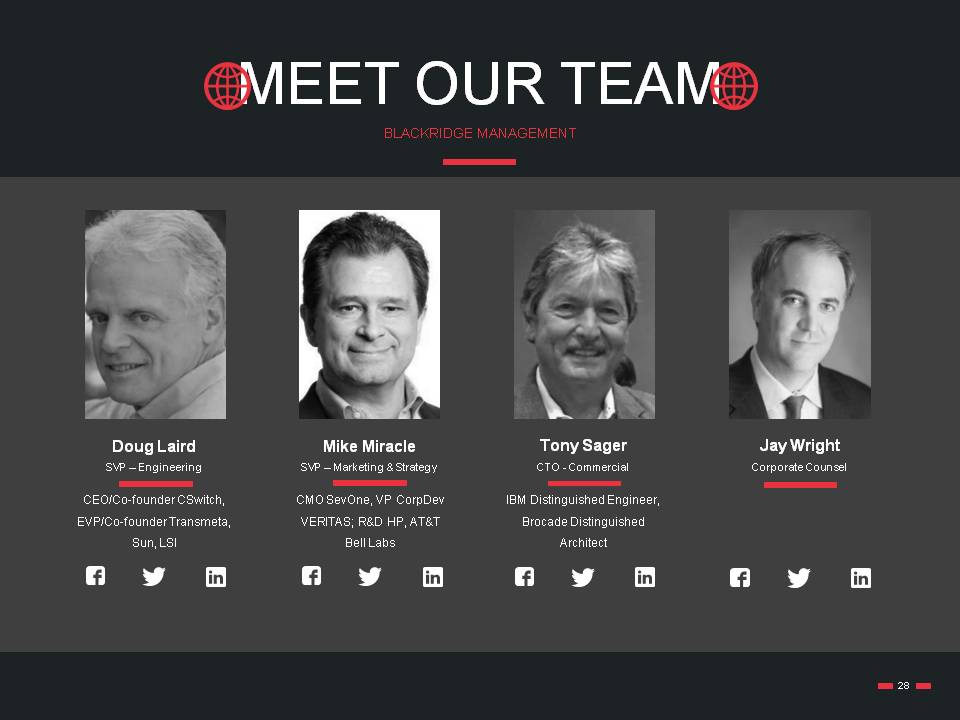
MEET OUR TEAM 28 BLACKRIDGE MANAGEMENT CEO/Co-founder CSwitch, EVP/Co-founder Transmeta, Sun, LSI Doug Laird CMO SevOne, VP CorpDev VERITAS; R&D HP, AT&T Bell Labs Mike Miracle IBM Distinguished Engineer, Brocade Distinguished Architect Tony Sager Jay Wright SVP – Engineering SVP – Marketing & Strategy CTO - Commercial Corporate Counsel

BALANCE SHEET & CAP TABLE 29 BALANCE SHEET: JUNE 30, 2017 C&CE $1,218,241 PREPAID EXPENSES $197,629 INTANGIBLE $6,402,456 TOTAL ASSETS $7,833,057 AP $2,110,533 ACCRUED INTEREST $1,576,402 LONG-TERM DEBT [CURRENT] $400,000 CONVERTIBLE NOTES [SHORT- TERM] $3,712,638 TOTAL LIABILITIES $21,986,947 CAPITALIZATION TABLE: COMMON SHARE EQUIVALENTS: COMMON STOCK 32,027,244 SERIES A DILUTIVE 37,838,180 WAGES & PAYABLES RSU TO BE ISSUED 20,635,960 OUTSTANDING WARRANTS AND OPTIONS 30,068,132 TOTAL 120,569,516

NETWORK SECURITY COMPS 30 COMPARISON OF NETWORK SECURITY CAPABILITIES Feature or Capability Transport Access Control Segmentation Firewalls Next Generation Firewalls NAC / 802.1x VPNs First Packet Authentication(pre-connection setup) Yes No No No No End-to-End Identity and Attribution Yes No No Same LAN segment only No Identity-based Policy Yes No Limited Yes Yes Multiple Enforcement Points Yes Yes Yes No No Requires Hardware Acceleration No No Yes No Yes Source NAT Tolerant Yes Yes Yes N/A Limited DoS Attack Protection Yes No Limited No No Supports In System Middle Boxes Yes Yes Yes No No Encrypted Data Payload Tolerant Yes Yes Limited N/A N/A Resource Application Identity Yes No No No No Trusted Resource Host Yes No Limited Limited No Topology Learning Yes No No No No End-to-End Trust Yes No No Limited No
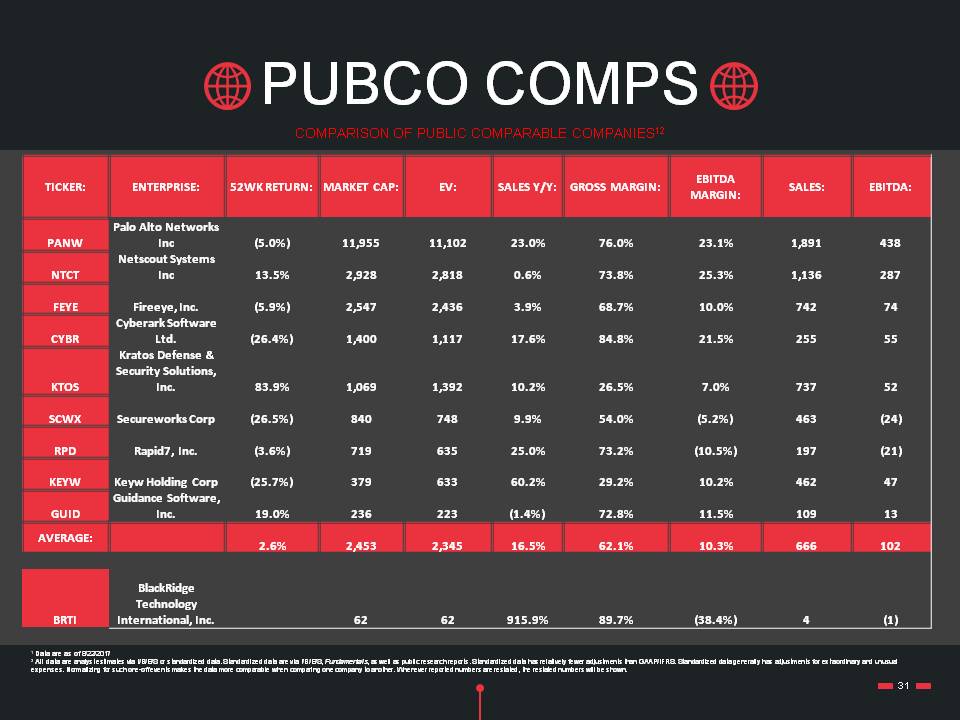
PUBCO COMPS 31 COMPARISON OF PUBLIC COMPARABLE COMPANIES12 TICKER: ENTERPRISE: 52WK RETURN: MARKET CAP: EV: SALES Y/Y: GROSS MARGIN: EBITDA MARGIN: SALES: EBITDA: PANW Palo Alto Networks Inc (5.0%) 11,955 11,102 23.0% 76.0% 23.1% 1,891 438 NTCT Netscout Systems Inc 13.5% 2,928 2,818 0.6% 73.8% 25.3% 1,136 287 FEYE Fireeye, Inc. (5.9%) 2,547 2,436 3.9% 68.7% 10.0% 742 74 CYBR Cyberark Software Ltd. (26.4%) 1,400 1,117 17.6% 84.8% 21.5% 255 55 KTOS Kratos Defense & Security Solutions, Inc. 83.9% 1,069 1,392 10.2% 26.5% 7.0% 737 52 SCWX Secureworks Corp (26.5%) 840 748 9.9% 54.0% (5.2%) 463 (24) RPD Rapid7, Inc. (3.6%) 719 635 25.0% 73.2% (10.5%) 197 (21) KEYW Keyw Holding Corp (25.7%) 379 633 60.2% 29.2% 10.2% 462 47 GUID Guidance Software, Inc. 19.0% 236 223 (1.4%) 72.8% 11.5% 109 13 AVERAGE: 2.6% 2,453 2,345 16.5% 62.1% 10.3% 666 102 BRTI BlackRidge Technology International, Inc. 62 62 915.9% 89.7% (38.4%) 4 (1) 1 Data are as of 8/22/20172 All data are analyst estimates via I/B/E/S or standardized data. Standardized data are via I/B/E/S, Fundamentals, as well as public research reports. Standardized data has relatively fewer adjustments than GAAP/IFRS. Standardized data generally has adjustments for extraordinary and unusual expenses. Normalizing for such one-off events makes the data more comparable when comparing one company to another. Whenever reported numbers are restated, the restated numbers will be shown.

PUBCO COMPS 32 TICKER: ENTERPRISE: MARKET CAP: EV: P/EPS: 2018 P/EPS: EV/EBITDA: 2018 EV/EBITDA: EV/SALES: 2018 EV/SALES: PANW Palo Alto Networks Inc 11,955 11,102 119.02x 35.91x 25.56x 19.60x 5.91x 4.83x NTCT Netscout Systems Inc 2,928 2,818 33.74x 13.89x 10.26x 8.13x 2.59x 2.28x FEYE Fireeye, Inc. 2,547 2,436 (14.56x) (499.29x) 32.74x 31.87x 3.29x 3.04x CYBR Cyberark Software Ltd. 1,400 1,117 46.81x 30.76x 20.39x 15.89x 4.39x 3.68x KTOS Kratos Defense & Security Solutions, Inc. 1,069 1,392 (164.38x) 37.23x 26.95x 19.38x 1.89x 1.78x SCWX Secureworks Corp 840 748 (24.73x) (62.66x) (31.26x) (511.98x) 1.61x 1.47x RPD Rapid7, Inc. 719 635 (19.05x) (34.76x) (30.69x) (41.00x) 3.23x 2.67x KEYW Keyw Holding Corp 379 633 (28.55x) 24.66x 13.43x 10.29x 1.37x 1.16x GUID Guidance Software, Inc. 236 223 84.81x 18.36x 17.76x 13.80x 2.04x 1.86x AVERAGE: 2,453 2,345 3.68x (48.43x) 9.46x (48.22x) 2.92x 2.53x BRTI BlackRidge Technology International, Inc. 62 62 1.88x 16.80x 3.19x 1 Data are as of 8/22/20172 All data are analyst estimates via I/B/E/S or standardized data. Standardized data are via I/B/E/S, Fundamentals, as well as public research reports. Standardized data has relatively fewer adjustments than GAAP/IFRS. Standardized data generally has adjustments for extraordinary and unusual expenses. Normalizing for such one-off events makes the data more comparable when comparing one company to another. Whenever reported numbers are restated, the restated numbers will be shown. COMPARISON OF PUBLIC COMPARABLE COMPANIES12

BUYING ENTERPRISE: TICKER: SELLING ENTERPRISE: TICKER: EXCHANGE: CONSIDERATION: PREMIUM TO MARKET CAP: P/S: SYMANTEC SYMC BLUE COAT [BAIN CAPITAL] N/A N/A $4.7B N/A 7.9X SYMANTEC SYMC LIFELOCK, INC. LOCK NYSE $2.4B 33% 3.6X CISCO CSCO APPDYNAMICS [APPD]1 N/A $3.7B N/A 18.9X INTEL INTC MOBILEYE MBLY NYSE $15.3B 40% 41.9X AVAST SOFTWARE [AVST]1 AVG TECHNOLOGIES AVG NYSE $1.4B 25% 3.4X FIREEYE FEYE ISIGHT PARTNERS N/A N/A $275M N/A 6.9X M&A COMPS 33 1 Not yet public2 Data are as of 8/22/20173 All data are analyst estimates via I/B/E/S or standardized data. Standardized data are via I/B/E/S, Fundamentals, as well as public research reports. Standardized data has relatively fewer adjustments than GAAP/IFRS. Standardized data generally has adjustments for extraordinary and unusual expenses. Normalizing for such one-off events makes the data more comparable when comparing one company to another. Whenever reported numbers are restated, the restated numbers will be shown. COMPARISON OF PUBLIC M&A TRANSACTIONS23

GRANTED PATENTS DISRUPTIVE, PATENT PROTECTED TECHNOLOGY 34

35 146Q1/2017 M&A TRANSACTIONSCybersecurity deals hit an all-time quarterly high of 146 deals in Q1’17, up 26% from the previous quarterly high. The trend held through Q2’17, which saw just one fewer deal [145 total] compared to Q1’17.1 $1.5BQ2/2017 EQUITY FUNDINGThe amount of disclosed equity funding to cybersecurity companies has also recently broken records, reaching an all-time quarterly high of $1.6B in Q2’17. 1 6+$100MM FUNDING ROUNDS Six companies obtained funding rounds of $100M+ in Q2’17. No other quarter on record has seen over four mega-rounds in cybersecurity. 1 Note that the current and projected funding totals for 2017 include only non-exited companies and therefore exclude deals such as the recent $2.29B Private Equity round raised by McAfee from the firm Thoma Bravo in April. 1 2 ANNUAL FINANCING TRENDS 428 Deal activity has increased steadily since 2012, with last year seeing a high of 428 deals, despite a small 6% drop in funding [down from a record $3.8B in 2015]. At the current run rate, both deals and dollars for 2017 are on track to rise to an all-time high. 1 MARKET INVESTMENT 1 CB Insights2 McAfee was acquired by Intel in 2010 and Intel retains 49% ownership of the company3 Through 6/30/2017; NOT annualized 3 3 IN MILLIONS

THANK YOU
